Updated June 10, 2024 to include DoNex Ransomeware decryptors from Avast.
It can happen to the best of us. You open an unknown attachment from an email, install sketchy software, or the latest unpatched 0Day is running wild on your Windows Server 2022. What’s next?
These are some of the possible options you have if your Windows Server has been hacked and encrypted. However, none of them are guaranteed to work or to be risk-free. Therefore, you should consult a professional IT expert before taking any action, and you should report the incident to the relevant persons and/or authorities.
Disconnect the networking
If the compromised system is still online, it could be used for outgoing DoS and other malicious attacks. You should disable networking on the server.
How to Enable or Disable Network Connections in Windows
Recover from backup
If you have a full image backup like IONOS Cloud Backup, then you could reinstall the operating system, reinstall the backup agent, and then restore your backup. However, you should first make sure that your backups are not infected or encrypted by the ransomware.
Downloading files from the cloud storage
You may also be able to restore your files from shadow copies, which are snapshots of your files created by Windows. However, some ransomware may delete or encrypt your shadow copies, so this option may not work. You can use tools such as ShadowExplorer to access and recover your shadow copies.
Identify the ransomware
Some ransomware variants may leave clues about their identity, such as ransom notes, file extensions, or encryption keys. You can use online tools such as ID Ransomware or No More Ransom to try to identify the ransomware and see if there is a known decryption tool available.
On July 7, 2024, Avast released a decryptor application for DoNex Ransomware, as well as it’s predecessors Muse, fake LockBit 3.0, and DarkRace.
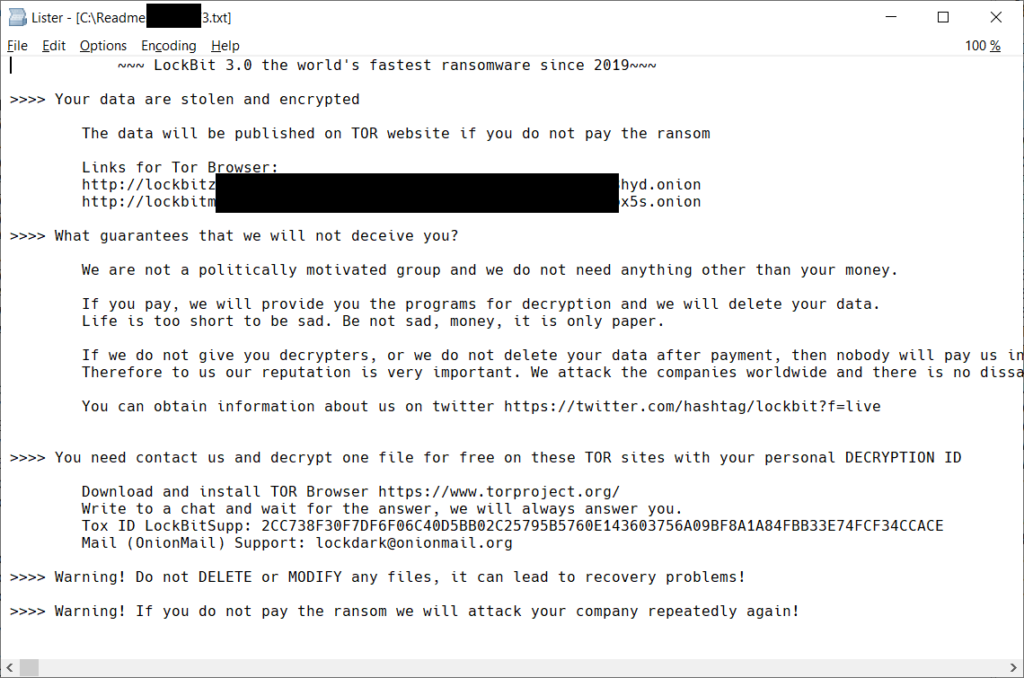
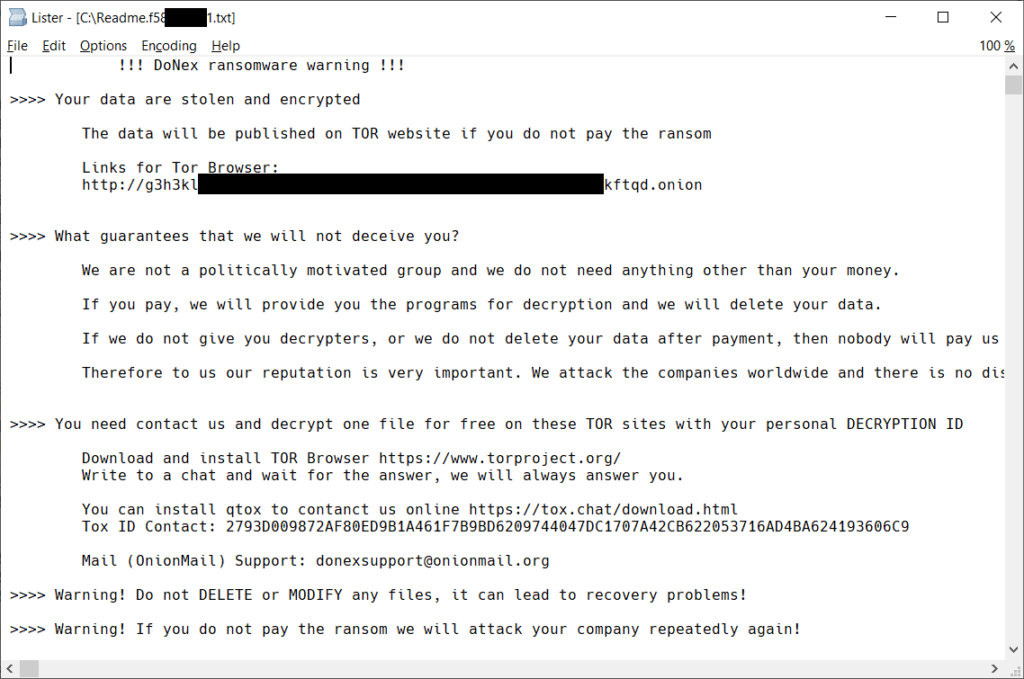
If you are affected by one of the DoNex ransomware attacks, first back up your encrypted file(s) (in the rare case the decryptor corrupts the file), and then download the application from Avast’s site here, or our mirror here.
Ransomware attacks are illegal and can be reported to the authorities. You can contact your local law enforcement agency. You can also contact a local FBI Field Office or the Internet Crime Complaint Center in the US for assistance. Reporting the incident may help the investigation and prosecution of the attackers, as well as prevent future attacks. You may also receive assistance or guidance from law enforcement on how to deal with the ransomware.