If your website or server is running slowly, you may fear that you are under a DoS or DDoS attack.
- Connect to the server. If possible, connect via SSH. In some cases, a server may unavailable via SSH. In this scenario, you want to check with your hosting/server provider to find if they have access to a VNC console, KVM console, or serial console. These tools allow remote access to a server even when it is not responding externally. It would be similar to plugging a monitor into the server.
- Find out how many active connections to the server to determine if a DoS/DDoS is occurring:
ss -s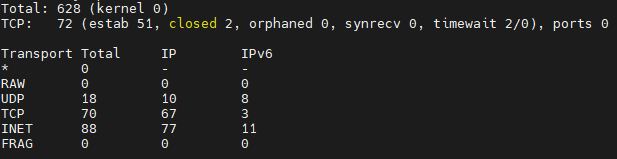
- Find out how many SYN attempts were received to determine if a SYN attack is occurring:
ss -tan state syn-recv | wc -l - Find the source IPs of the attacks
DoS/DDoS on website:ss -tan state established | grep ":80|:443" | awk '{print $4}'| cut -d':' -f1 | sort -n | uniq -c | sort -nr
DoS/DDoS anywhere:lsof -i -n -P | awk '$9 ~ /.->./ {split($9,a,"->"); split(a[2],b,":"); print b[1]}' | sort | uniq -c | sort -nr
SYN attack:ss -tan state syn-recv - Find out which websites are being targeted:
for log in /var/www/vhosts/system/*/logs/*access*log; do echo -n "$log "; tail -n10000 "$log" | grep -c 123.456.7.89; done | sort -n -k2 - Block IP(s) on Ubuntu/Debian:
sudo ufw deny from 123.456.7.89 to any
Alternatively, to add the top 5 IPs with the most connections to your firewall deny ruleset:ss -tan state established | awk '{if ($4 ~ /[0-9]+.[0-9]+.[0-9]+.[0-9]+:[0-9]+/) print $4}' | cut -d':' -f1 | sort -n | uniq -c | sort -nr | xargs -I{} ufw deny from {}
Block IP(s) on CentOS/Fedora/RHE:sudo firewall-cmd --permanent --add-rich-rule="rule family='ipv4' source address='xxx.xxx.xxx.xxx' drop"